Reverse Proxies
The objective of this article is to explain what a reverse proxy is, starting from a relatively simple example.
Let's consider the situation in the diagram below:
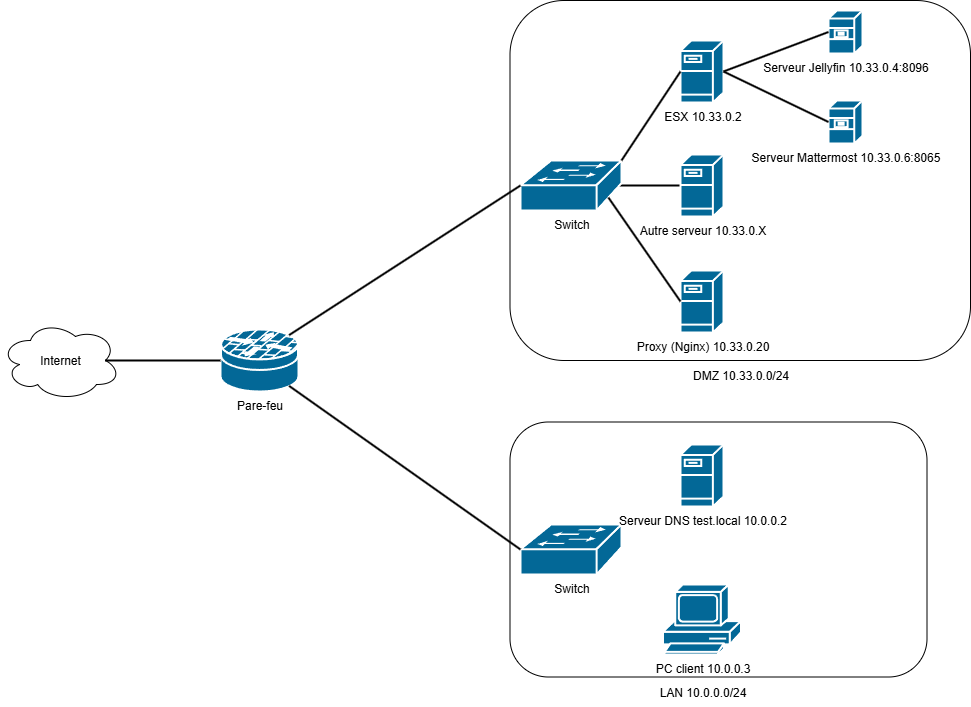
The firewall rules allow LAN users to access the ESX virtual servers in the DMZ. For example, to access the Jellyfin media server, the user can type http://10.33.0.4:8096 or http://jellyfin.test.local:8096 (if the DNS server has this record).
However, these methods only work locally, so what about access from the internet with the fictional domain test.com?
This is where things get complicated... The web services present on the servers use many ports that would need to be opened at the router level, and it's not very practical to specify the port each time you want to load a site. This is where reverse proxies find their full utility.
Its role (at least in our example) is to serve as a single gateway to all web services, thus allowing port rewriting and access to different services from a single IP address.
Let's take an example to make this clearer: Suppose the public IP address of our example is 86.198.25.280 (yes, this is not a real IP address, it's on purpose). If we want to access the Mattermost server, we can type in the navigation bar http://86.198.25.280:8065 which should redirect us to the Mattermost login page if port 8065 is open. With a reverse proxy, it's enough (if our domain has this A record) to create the record http://mattermost.test.com -> http://10.33.0.6:8065 and we should land on the login page by requesting http://mattermost.test.com. It's magic...
Therefore, the only ports to open are ports 80 and 443 to the proxy, which adds an additional security layer to your infrastructure whose topology will be harder to determine.
But reverse proxies have more than one string to their bow as an essential web tool. They can serve as TLS termination proxies, meaning the connection between the server and the proxy is done in HTTP and the connection between the proxy and the internet in HTTPS (assuming you have valid TLS certificates, which is quite easy to obtain for free thanks to Let's Encrypt).
If we return to our example, when we request access to the URL https://mattermost.test.com, the traffic between the server on 10.33.0.6, port 8065, and the reverse proxy will be done in HTTP, but the traffic between the reverse proxy and the destination web browser (the site can possibly be proxied through Cloudflare, but this doesn't change much) will be done securely.
