The OSI Model, "the stage"
This article inaugurates the series "The Dance of Protocols," where we explore how network protocols collaborate to create our modern infrastructures.
Divide and Conquer
Do you know the saying "divide and conquer"?
Well, if you've had history classes, you've probably heard it before. But did you know that this principle is true for many other aspects of life, particularly in networks?
Now you're probably wondering what I smoked before writing this article, and the answer is "absolutely nothing" (yes I know, it's surprising). The separation of the network into several layers, you experience it every day, and this without even realizing it. It's actually what makes your phone work just as well on Wi-Fi as on 5G (or 4G if your phone isn't compatible).
But then, what's the point of separating the network into layers?
It serves to guarantee the independence of protocols from lower layers. What I just told you is a basic principle, normally inviolable, of the model I'm going to present to you.
To understand this principle of layer independence, let's take a fairly simple example.
A Small Analogy
Suppose I have friends in Canada and I want to send them a letter (because apparently we're in the 1930s). What would be the steps? The steps are as follows: I write the letter, I post it, the letter is transported to international shipping headquarters, the letter crosses the Atlantic by boat, it's transported to the local post office, then delivered and finally read by my friends. Easy, right?
Layer independence
Now, if I change boat transport to airmail service, do the other steps change? Not at all, I would still have to write my letter, I would still have to post it, etc.... And all this is thanks to the independence principle of these famous layers.
Well, we'll see that this principle isn't always true, in our case, switching to telegram would have changed some intermediate steps but not those at the ends.
Okay, enough talk about related subjects, let's move on to networks.
The Seven Layers
The model we're going to talk about dates from 1984 (yes it's old) and was amended in 1994. It's the OSI model for Open Systems Interconnection and it was developed by an agency (not very well known...) called ISO. It's divided into 7 layers, each having one or more specific functions and associated protocols. The name of the data transiting on each layer is also different depending on which one we consider.
In terms of vocabulary, a layer provides services to upper layers and relies on services from lower layers. Additionally, data passed by upper layers is said to be encapsulated and data from lower layers is de-encapsulated.
The 7 layers are, from bottom to top, "Physical," "Data Link," "Network," "Transport," "Session," "Presentation," and "Application."
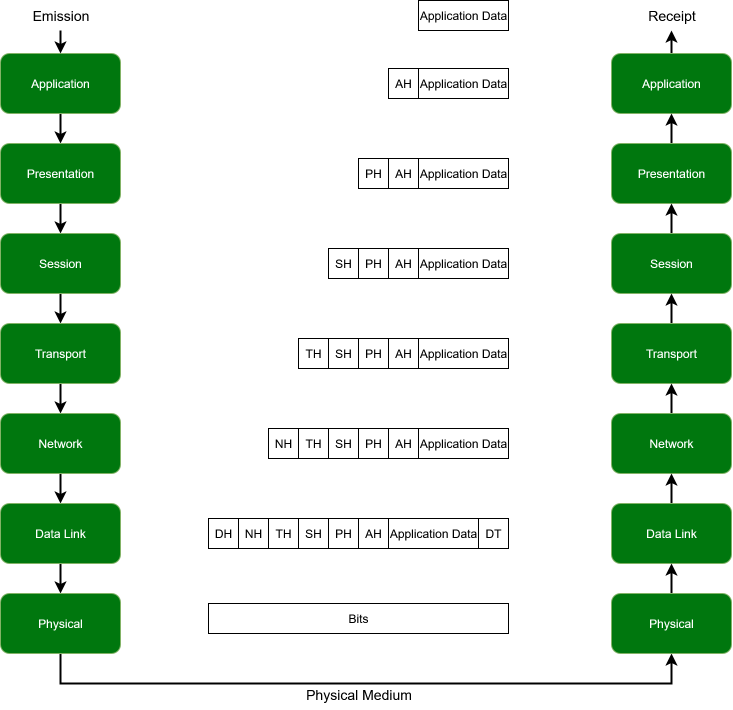
The OSI model with encapsulation and de-encapsulation principles
Network Layers (1-4)
The physical layer is responsible for ensuring reliable transmission of bits over a physical medium (a cable, optical fiber, waves in the case of Wi-Fi or 5G, ...).
The data link layer has two functions: it manages access to the medium, particularly information collision problems, and is also responsible for controlling the integrity of frame transmission through error detection and correction codes.
The network layer is responsible for determining the paths taken by packets between their source and destination. This includes congestion control, which aims to avoid traffic jams, prevent saturation of network node input buffers, and account for temporary unavailability of certain links.
The transport layer is responsible for the reliability of transmission between sender and receiver. It notably handles packet segmentation into smaller segments and segment retransmission in case of error.
Application Layers (5-7)
I'd be tempted to present the remaining 3, but they're not strictly part of the networking domain. They would be classified more as "application" layers that allow processing data arriving from or going to layer 7 to transform it appropriately.
Associated Protocols
As I told you, each layer also has a myriad of specific protocols, some of which even spill over to other layers...
For layer 1, we find obsolete protocols like SDH or PDH and more modern protocols like Wi-Fi or xDSL.
In layer 2, we find the mythical Ethernet protocol, which you've surely heard of when someone presented you with a box with n 2.5Gbit/s Ethernet ports on it (sigh...). Here too, we find older protocols, like X.25 which was notably used by Minitel (R.I.P).
In layer 3, we most often find a protocol that's universal today: IP (v4 or v6, we don't care for now). We also find certain routing protocols that operate directly at the network level, like RIP for Routing Information Protocol or OSPF for Open Shortest Path First. RIP is an obsolete protocol that's not really used nowadays, except in network courses since it's very simple to understand and manipulate.
And finally, for layer 4, the best-known protocols are TCP and UDP. For now, I won't detail the difference between the two, this will be the subject of a future article.
Know also that some protocols can span multiple layers, like MPLS (for Multi-Protocol Label Switching) which operates at layer three while using layer 2 switching mechanisms. We say that MPLS is a layer 2.5 protocol, which is quite painful since it means the two layers are not independent in this case.
Some Exceptions
And precisely, this brings us back to a remark I made earlier about exceptions to this great principle of independence. We just saw that MPLS violates the principle, but Ethernet does too since it includes a field called Ethertype in its header allowing it to detail the nature of the upper layer protocol contained in the frame. In reality, there are a myriad of protocols that violate it, however, we don't have time to detail them all if I want this article not to be 10,000 lines long.
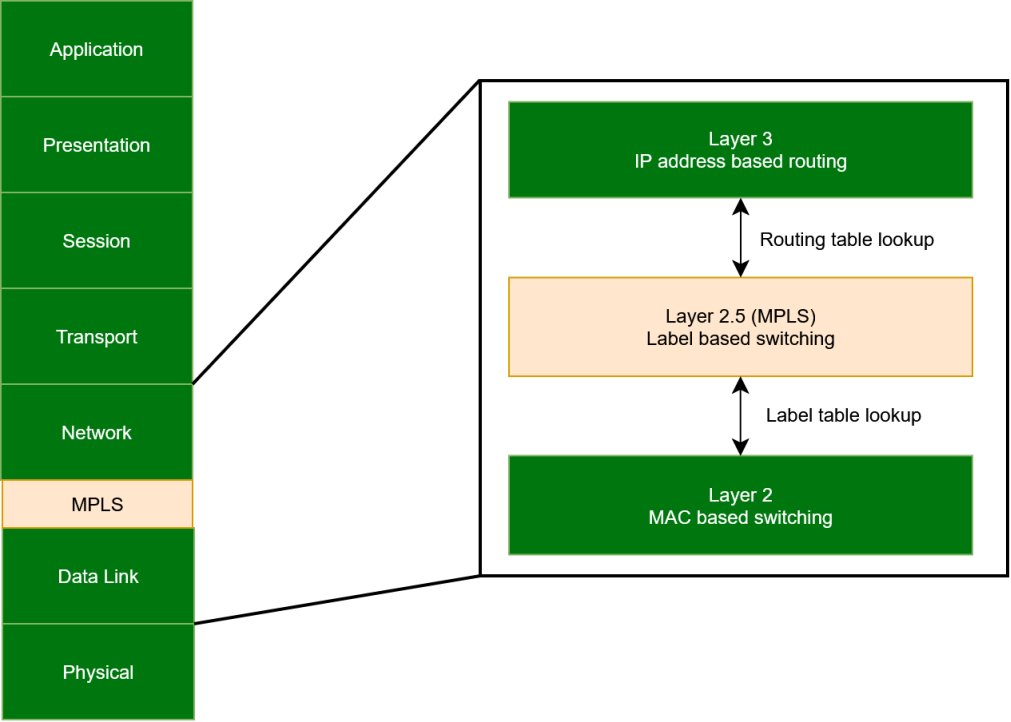
The MPLS exception
Conclusion
The OSI model gives us the common vocabulary to understand how network protocols interact. Even if some protocols violate the independence principle (MPLS, Ethernet, ...), this model remains one of the references (along with the TCP/IP model) for structuring our understanding of networks.
Now that the "stage" is set, we can explore how each protocol plays its role. In the next article in the "Dance of Protocols" series, we'll discover Ethernet, the basic rhythm that makes our modern local networks dance.
Next episode: Ethernet: "the metronome" - How this layer 2 protocol orchestrates our local communications.
